DevSecOps: Building Security Into Every Stage of Development
In our previous post, we discussed what makes DevSecOps the superhero of secure software development. If you haven’t seen it, catch up here.
Today, let’s examine why treating security as a final checklist item exposes organizations to growing risks – and why a smarter approach means integrating security at every stage of development.
The DevSecOps Mindset: Security as a Shared Responsibility
DevSecOps isn’t just a toolset or a process; it’s a culture shift. Instead of leaving security for a final review, resilient organizations embed it from the very start. The result? Fewer vulnerabilities, streamlined compliance, and software that inspires trust.
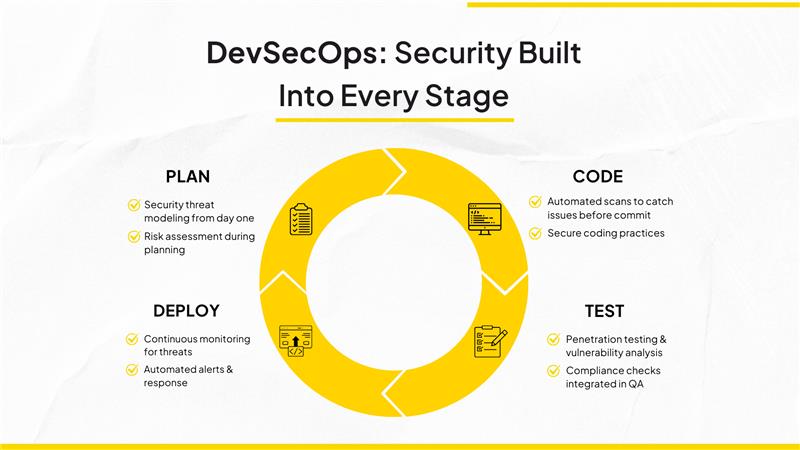
DevSecOps in Practice: How Every Phase Becomes Secure
- Plan
From the very beginning of a project, security considerations must be embedded into planning. Security experts actively participate in architectural reviews and requirements discussions, ensuring potential vulnerabilities are identified early. Threat modeling becomes a standard part of project kickoffs, helping teams anticipate and design defenses against likely attack vectors. This proactive involvement shifts security left, reducing costly fixes later and aligning the entire team on security goals from day one. - Code
Secure coding is an ongoing activity, not a one-time checkpoint. Automated static and dynamic analysis tools are integrated into the development pipeline, scanning code with every commit. This continuous feedback loop allows developers to catch, understand, and fix vulnerabilities immediately, preventing issues from becoming entrenched. By coupling automated scans with coding best practices and peer reviews, teams raise the overall quality of their software while maintaining rapid development pace. - Test
Security testing evolves beyond infrequent, siloed activities to become an integral, continuous process. Penetration tests, vulnerability scans, and compliance validations are embedded within continuous integration and deployment (CI/CD) pipelines, ensuring every build undergoes rigorous evaluation before release. This approach reduces the risk of surprises at later stages and enables teams to rapidly identify and mitigate emerging security gaps, strengthening the overall security posture of the application. - Deploy
Security vigilance extends into production environments through continuous monitoring tools that detect anomalies, unauthorized access attempts, and configuration drifts. Automated alerting mechanisms notify teams of suspicious activity, enabling immediate response to potential threats. Combined with secure infrastructure provisioning and secrets management, this active defense stabilizes the deployment environment, supporting trustworthiness, compliance, and uninterrupted service.
Why This Matters
Embedding DevSecOps end-to-end means:
- Faster release cycles with fewer surprises
- Lower risk of breaches and costly compliance fixes
- Greater alignment across development, operations, and security teams
- Stronger customer confidence in your software
Tools for Action: Get Your DevSecOps Quick Start Checklist
Ready to move from theory to action?
This checklist helps your team implement key DevSecOps practices, step by step.
Partner With NAKS Consulting
At NAKS Consulting, we help organizations shape secure development lifecycles from the ground up.
Whether you’re modernizing legacy platforms or building greenfield apps, our team is ready to make DevSecOps work for you.
Security isn’t just the end of your development-it’s the foundation. Let’s build resilient software, together